Still Leaking Secrets in Git? Let’s Fix This Before It’s Too Late
Still Leaking Secrets in Git? Let’s Fix This Before It’s Too Late
- Written by:-
- Yash Rathod
- DevSecOps
- No Comments
.gitignore files. To avoid these risks, it’s important for developers to follow best practices—like using environment variables, secret scanning tools, and automated CI/CD pipelines that can catch and prevent secrets from being committed to the code.Common Risks of Hardcoded Secrets in Repositories
- Unauthorized Access: Exposed credentials can allow attackers to access sensitive systems and data.
- Data Breaches: Secrets in public repositories are often quickly scanned by attackers, leading to data breaches.
- Service Disruptions: Misused credentials can disrupt services, leading to financial and reputational damage.
- Supply Chain Attacks: Hardcoded secrets in source code are an entry point for software supply chain compromises.
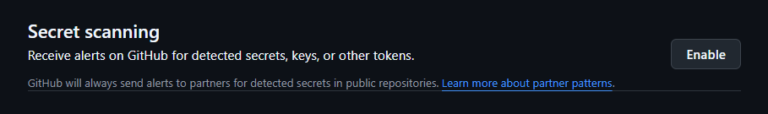
Secret Scanning:
- GitHub automatically scans public repositories for exposed credentials such as API keys, tokens, and passwords. It identifies common secret patterns (like AWS access keys or Google Cloud credentials) and alerts repository owners or contributors about the exposure.
- For private repositories, this feature is available through GitHub Advanced Security, where organizations can continuously scan for secret leaks across their private codebases.
- GitHub has partnered with cloud providers and third-party services to automatically revoke or reset compromised secrets when detected in public repositories, reducing the risk of further exploitation.
- Use
.gitignore: Add sensitive files (like config files with secrets) to.gitignoreto prevent them from being committed to the repository. - Leverage GitHub Actions secrets: Store sensitive data securely within GitHub Actions’ secrets storage instead of hardcoding them.
- Enable secret scanning: If you’re using private repositories, consider subscribing to GitHub Advanced Security to enable secret scanning across all repositories.
- Public repositories receive secret scanning for free under GitHub’s Free tier plan.
- While for private repositories GitHub Advanced Security (Enterprise Version) plan includes secret scanning, code scanning, and other advanced features. This is part of GitHub’s premium Enterprise Cloud or GitHub Enterprise Server offerings.
Secret Detection:
- Secret Detection in GitLab helps developers avoid accidentally exposing sensitive information, such as private keys, tokens, and passwords (collectively called “secrets”), in Git repositories. Secrets are vital for accessing external resources like databases, APIs, and CI/CD services, and if exposed, they can allow unauthorized users to impersonate legitimate ones. GitLab provides multiple methods to detect secrets and prevent unauthorized access.
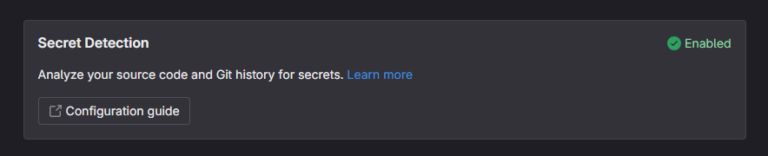
Secret detection methods available in GitLab:
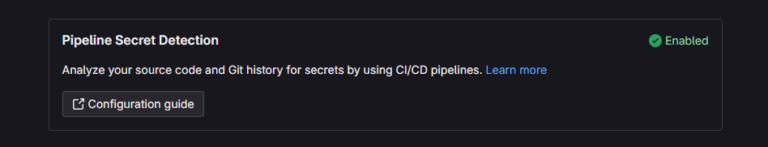
1. Pipeline Secret Detection:- This method works during the execution of the CI/CD pipeline.
- It scans all text files for sensitive patterns, regardless of the language or framework.
- While this method provides detailed reports of any secret found, it cannot block the push, meaning that it is reactive rather than preventive.
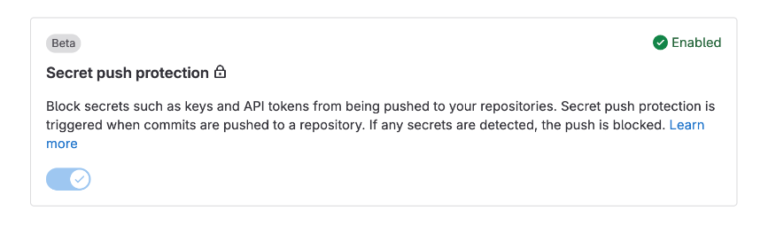
- This method runs when a developer pushes changes to a remote Git branch.
- It scans for secrets in real-time and can reject the push if a secret is detected, providing preventive protection.
- This feature is particularly useful in preventing secrets from ever making it into a remote repository.
- This runs in the user’s browser and warns them if they are about to push content that contains potential secrets.
- It adds another layer of protection by alerting users before secrets are pushed, helping developers catch mistakes early in the process.
- GitLab offers Secret Detection across all its tiers: Free, Premium, and Ultimate. However, the more advanced features and detailed security insights are unlocked in the higher tiers.
- GitLab.com (Cloud Service): Secret detection can be used directly in GitLab’s SaaS offering.
- Self-Managed GitLab: Secret detection is available for companies hosting their GitLab instances.
- GitLab Dedicated: Secret detection can also be used in GitLab’s dedicated hosting option for large enterprises.
- Bitbucket automatically scans repositories for sensitive data like passwords, tokens, private keys, and other secrets when new commits are pushed.
- When a secret is detected in the code, Bitbucket triggers notifications to alert the involved parties, helping teams respond quickly to remove or revoke the compromised secret.
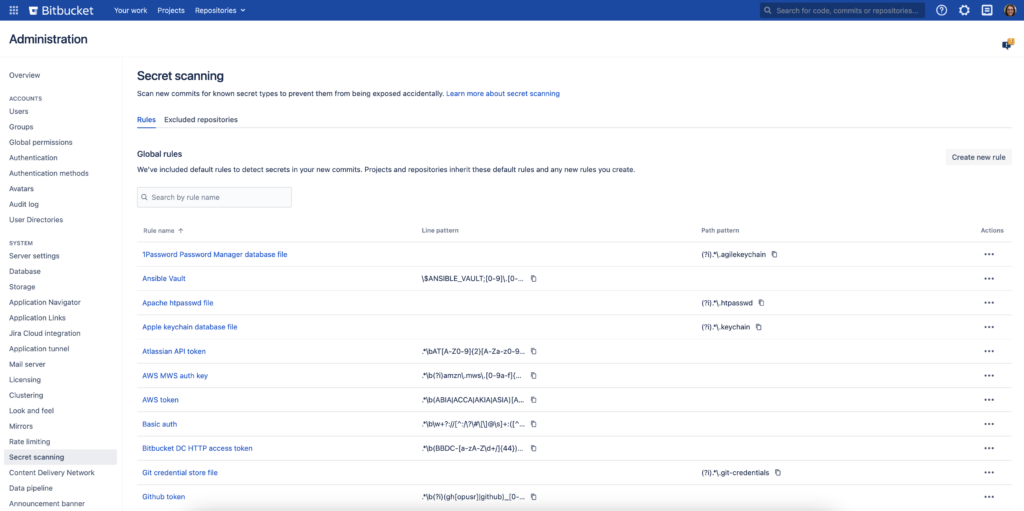
Additional Security Measures:
- Environment Variables: Like GitHub and GitLab, Bitbucket encourages the use of environment variables in Bitbucket Pipelines to store sensitive information securely. This prevents secrets from being hardcoded in the source code.
- Third-Party Tools: While Bitbucket’s built-in secret scanning offers essential protection, organizations can also integrate third-party tools like Snyk and GitGuardian for more advanced security scanning, real-time monitoring, and proactive alerts.
- Default Availability:
- Secret scanning is enabled by default in all self-hosted Bitbucket instances (Bitbucket Server and Bitbucket Data Center).
- This feature is available across all tiers for on-premise versions but must be managed through the Bitbucket configuration (
bitbucket.propertiesfile).
- Cloud Version:
- Currently, Bitbucket Cloud does not offer native secret scanning like its on-premise counterparts. However, teams using Bitbucket Cloud can integrate third-party tools like GitGuardian, Snyk, or SonarQube to enable secret detection and scanning functionality.
- Enterprise and Premium Plans:
- For Bitbucket Data Center, the enterprise-level on-premise version, secret scanning is available by default with additional support for audit logs and notifications.
- In premium plans of Bitbucket Cloud, secret scanning must be implemented via third-party integrations. However, advanced permissions, merge checks, and security measures (like environment variable encryption in pipelines) are available out of the box.
GitLeaks is a powerful SAST (Static Application Security Testing) tool specifically designed to detect and prevent hardcoded secrets like passwords, API keys, and tokens in Git repositories. It offers an easy-to-use, all-in-one solution to scan for secrets, whether they were committed in the past or are present in current code. By integrating GitLeaks into your development pipeline, you can proactively monitor repositories and identify potential security risks before they reach production, ensuring that sensitive data remains protected from accidental exposure.
Key Features:
- Comprehensive Detection: Scans both current code and commit history for any hardcoded secrets, ensuring no sensitive information is overlooked.
- Customizable Rules: Provides predefined patterns for common secrets while allowing users to create custom rules tailored to specific organizational needs.
- Ease of Use: Simple setup and integration make it easy to implement in CI/CD pipelines for continuous security monitoring.
- Cross-Platform Support: Compatible with various Git hosting services, including GitHub, GitLab, and Bitbucket.
Availability:
GitLeaks is open-source and free to use, making it an accessible option for developers and organizations aiming to enhance the security of their codebases without the need for premium versions.
To prevent secret leaks in your codebases and infrastructure, a number of modern tools and practices have been developed. These tools focus on automatically detecting, scanning, and protecting sensitive information like API keys, credentials, and secrets before they can be leaked. Here are some of the latest tools and techniques for preventing secret leaks:
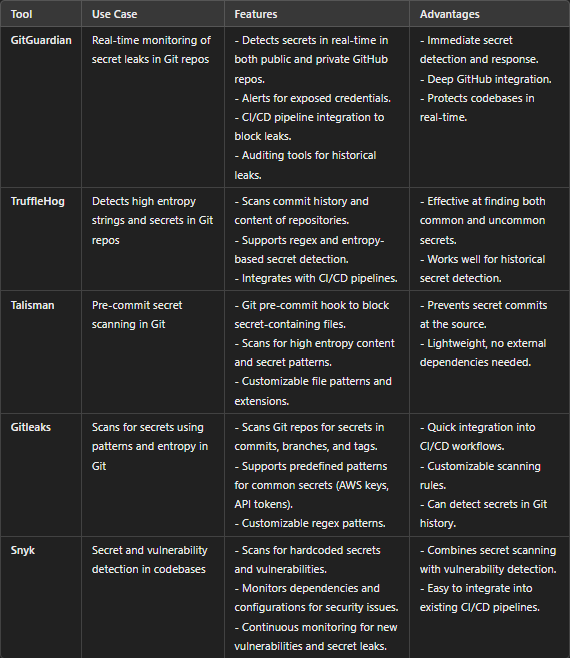
Summary of Key Advantages:
- GitGuardian: Best for real-time monitoring and continuous protection, with strong GitHub integration. It’s ideal for both private and public repositories.
- TruffleHog: Known for detecting high entropy strings and searching through commit histories. It’s excellent for scanning both current and past commits for potential secrets.
- Talisman: Proactive tool that blocks secrets at the commit stage via pre-commit hooks, ideal for developers who want to stop leaks at the source.
- Gitleaks: Effective for deep scanning of Git repositories using predefined patterns. It’s flexible for integrating into automated CI/CD workflows.
- Snyk: Combines secret scanning with broader vulnerability detection, making it a great choice for securing both code and dependencies in a single tool.
These tools are all designed to detect and prevent secret leaks, but their focus and integrations differ, allowing you to choose the one that fits your development and security processes.
Preventing secret leaks is essential for maintaining security across development workflows. Platforms like GitHub, GitLab and Bitbucket offers built-in or integrative tools like secret scanning, secure file storage, and notifications to help detect and prevent the exposure of sensitive information. By utilizing features such as Microsoft Defender for DevOps or GitHub Advanced Security, enforcing branch policies, and leveraging secure secret management solutions like Azure Key Vault, organization can protect their code and minimize risks associated with secret leaks.
