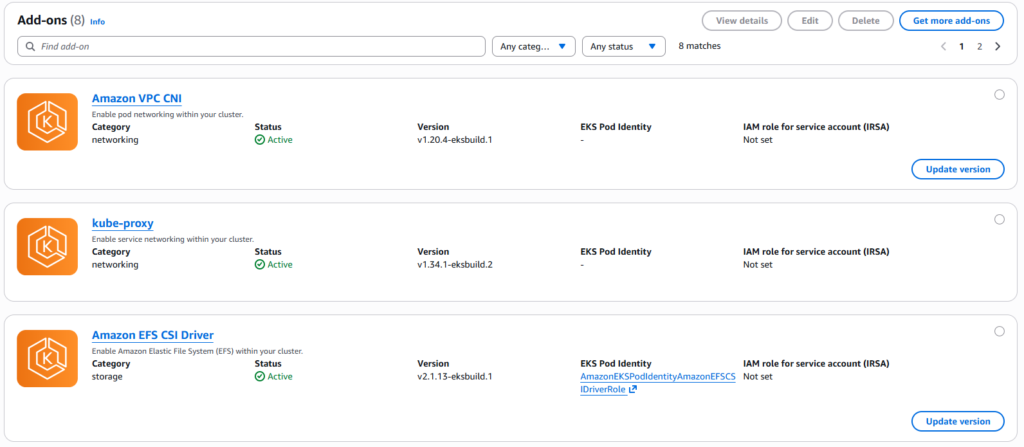
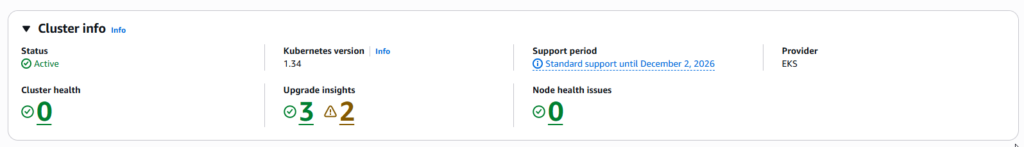
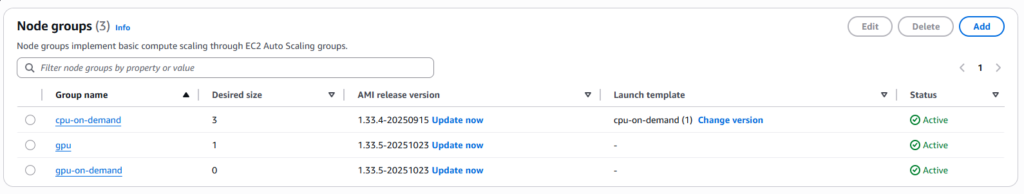
Upgrading EKS clusters involves careful orchestration of multiple components, thorough planning, comprehensive testing and continuous monitoring. Success depends not on following a rigid checklist, but on understanding the underlying principles: maintain application availability through PDBs and proper configurations, validate thoroughly in staging environments, backup everything, sequence components correctly and monitor continuously post-upgrade.
By following these best practices, you transform EKS upgrades from fearsome operations that keep teams up at night into well-understood, repeatable processes that you can execute confidently. The investment in planning, tooling and testing upfront pays dividends through reduced risk, faster deployment and greater overall reliability. Remember that every upgrade is also a learning opportunity, document issues, refine your processes and continuously improve your upgrade procedures with each iteration. As your team gains experience and confidence, you can gradually adopt more aggressive upgrade strategies, but always maintain the fundamental discipline of testing, validation and careful sequencing that ensures cluster stability and application availability.