- Written by:-
- Keval Kanpariya
- AWS, DevSecOps
- No Comments
Managing security and compliance across multiple AWS accounts can be challenging, especially when each account represents a different product, environment, or team structure. While isolating environments (such as production, staging, and development) in separate accounts improves security by limiting lateral movement, it also creates operational complexity. This post explores how to centralize security using native AWS services in a multi-account setup.
Why Centralizing Security in AWS Multi-Account Environments Matters
Centralizing security functions offers several key benefits:
- Unified Visibility: Consolidated monitoring and logging across all accounts enhance incident detection and response capabilities.
- Consistent Policy Enforcement: Ensures uniform security policies—such as identity management, compliance, and configuration standards—across every account.
- Operational Efficiency: Reduces administrative overhead and streamlines security operations by leveraging AWS Organizations to manage multiple accounts from a central location.
Leveraging AWS Organizations
AWS Organizations enables centralized management and governance of multiple AWS accounts under a single “management” or “root” account. With it, the following capabilities are available:
- Consolidate Billing: Provides a single view of all costs.
- Enforce Policies: Uses Service Control Policies (SCPs) to apply consistent rules and restrictions across accounts.
- Delegate Administration: Assigns specific administrative tasks (such as security, logging, and monitoring) to specialized accounts—often called “Security” or “Log Archive” accounts.
Core AWS Services for Centralized Security
Amazon S3 is a versatile solution for archiving a wide range of data types. Below are three critical categories of data that can be archived on S3 to ensure long-term retention, cost savings, and easy retrieval when needed.
1. AWS Security Hub
Security Hub aggregates security alerts from multiple AWS services including Guard Duty, Amazon Inspector, Macie, IAM Access Analyzer, and more into a single console. This enables organizations to:
- Correlate Events from various sources in one place.
- Identify Compliance Gaps based on AWS and industry standards.
- Leverage Partner Integrations for extended functionality (e.g., SIEM tools).
Security Hub Integration Diagram
Below is an example architecture showing how Security Hub can be used as the central hub in a multi-account setup:
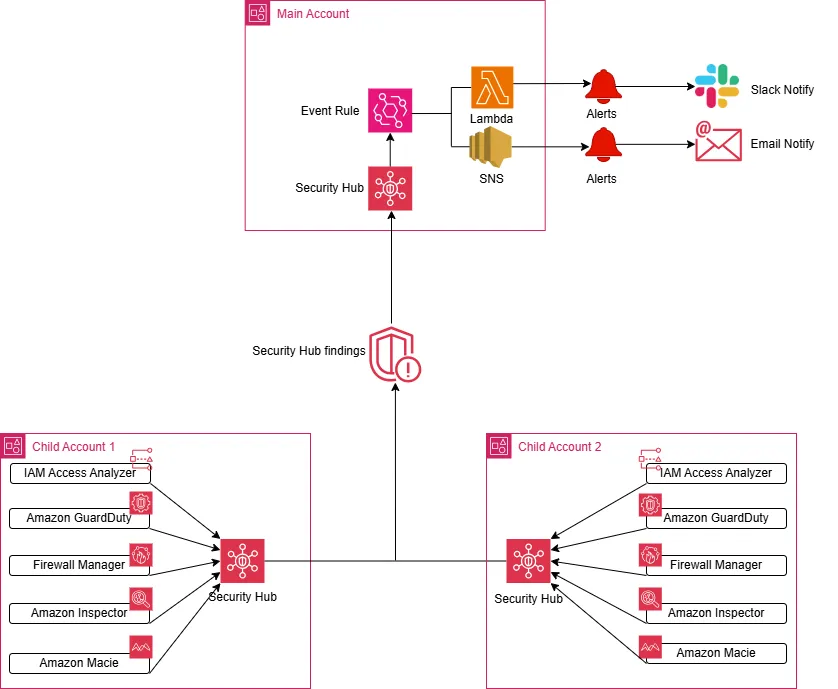
In this setup:
- Main (Security) Account runs Security Hub as the delegated administrator.
- Child Accounts each have Security Hub enabled, feeding findings (GuardDuty, Inspector, Macie, IAM Access Analyzer, etc.) back to the main account.
- Notifications (Slack, email, etc.) can be triggered through services like SNS or Lambda in the main account.
2. AWS IAM & IAM Identity Center
Secure access is the foundation of any security strategy. AWS Identity Center (formerly AWS SSO) allows:
- Centralized management of user identities in a single location (using the built-in directory or external identity providers like Okta, Active Directory, etc.).
- Standardized permission sets across accounts.
- Customizable session timeout policies for different environments.
3. AWS CloudTrail
AWS CloudTrail records all API calls and activities across AWS accounts. Enabling an organization-wide trail:
- Centralized log storage in a dedicated S3 bucket.
- Simplified audits, compliance reporting, and forensic analysis.
- Enhanced security through log file validation and KMS encryption.
4. Amazon GuardDuty
Amazon GuardDuty provides real-time threat detection by continuously analyzing AWS account activity and network traffic for malicious activity. It uses data sources such as:
- AWS CloudTrail events to detect unauthorized API calls or unusual user behavior.
- VPC Flow Logs to identify suspicious network traffic.
- DNS logs to uncover attempts to contact malicious domains.
- EKS audit logs to detect anomalies in containerized workloads.
5. AWS Config
AWS Config continuously records and evaluates the configurations of AWS resources against desired configurations. By creating a Config aggregator, it is possible to:
- Monitor compliance across multiple AWS accounts and regions.
- Detect and remediate non-compliant resources automatically.
- Integrate with Security Hub and other AWS services for holistic security insights.
6. Amazon Inspector
Amazon Inspector automates vulnerability assessments for EC2 instances and container images. With Inspector:
- Regular Scans identify potential security risks.
- Severity-Based Alerts help prioritize remediation efforts.
- Deep EC2 Inspection can uncover application-level vulnerabilities (Python, Java, Node.js, etc.).
Conclusion
Centralizing security in an AWS multi-account environment is essential for maintaining a robust and scalable security posture. Leveraging AWS Organizations along with native services—such as IAM Identity Center, CloudTrail, GuardDuty, Security Hub, Config, and Inspector—provides:
- Enhanced Visibility across all AWS accounts.
- Consistent Policy Enforcement aligned with organizational requirements.
- Streamlined Operations that reduce complexity and administrative burden.
A centralized approach enhances security management, ensuring long-term efficiency and resilience.
