Establishing a Secure Private Connectivity Between On-Premise and AWS EC2
- Written by:-
- Pradip Khuman
- No Comments
In today’s hybrid cloud environments, organizations need secure and reliable communication between on-premise infrastructure and cloud resources like Amazon EC2 instances. Whether you’re migrating legacy applications, accessing sensitive services, or extending internal networks into AWS, a private connection is critical. AWS Site-to-Site VPN provides a cost-effective and secure solution to achieve this. Additionally, for individual users or smaller setups, the AWS VPN Client can be used to connect securely to EC2 instances. This blog explores both approaches, detailing their benefits, architecture, and step-by-step implementation.
What is AWS Site-to-Site VPN?
AWS Site-to-Site VPN establishes a secure, encrypted IPsec tunnel between your on-premise network and an Amazon Virtual Private Cloud (VPC) over the public internet. It ensures data privacy and integrity during transit, making it ideal for hybrid cloud setups. The connection uses a Virtual Private Gateway (VGW) or Transit Gateway on the AWS side and a Customer Gateway (CGW) on the on-premise side.
What is AWS VPN Client?
The AWS VPN Client is a software solution for individual users or small teams to connect securely to AWS resources over a client-to-site VPN. It’s particularly useful for remote workers or administrators needing secure access to EC2 instances in a VPC without exposing them to the public internet.
Use Cases
Site-to-Site VPN:
Migrate on-premise applications to EC2 while maintaining private connectivity.
Enable secure access to internal APIs, databases, or services hosted on EC2.
Extend on-premise networks to AWS for hybrid applications, such as payroll systems interacting with cloud-hosted dashboards.
AWS VPN Client:
Provide remote employees or administrators secure access to EC2 instances.
Connect laptops or desktops to private subnets in a VPC for development or management tasks.
Securely access internal tools or virtual desktops hosted on EC2.
Architecture Overview
Below is a comprehensive architectural overview that illustrates the fundamental differences in how AWS Site-to-Site VPN operates compared to the AWS VPN Client. This overview highlights the distinct working mechanisms, connectivity flows, and use cases associated with each VPN solution.
Site-to-Site VPN
+------------------+ +---------------------------+
| On-Premise LAN | <-- VPN over Internet --> | AWS Virtual Private Cloud |
| (e.g., Office) | | (VPC) |
| 10.0.0.0/16 | | 172.31.0.0/16 |
+------------------+ +---------------------------+
| |
Router/Firewall EC2 Instances in Private Subnet
| |
+--------------------+ +-----------------------------+
| Customer Gateway | <== IPsec Tunnel ==> | Virtual Private Gateway |
| (CGW) | | (VGW or Transit Gateway) |
+--------------------+ +-----------------------------+AWS VPN Client
+------------------+ +---------------------------+
| User Device | <-- VPN over Internet --> | AWS Virtual Private Cloud |
| (Laptop/PC) | | (VPC) |
| | | 172.31.0.0/16 |
+------------------+ +---------------------------+
| |
AWS VPN Client EC2 Instances in Private Subnet
| |
+--------------------+ +-----------------------------+
| Client Endpoint | <== IPsec Tunnel ==> | Client VPN Endpoint |
| (User Device) | | (AWS-managed) |
+--------------------+ +-----------------------------+How to Set It Up: Step-by-Step Guide
Setting Up Site-to-Site VPN
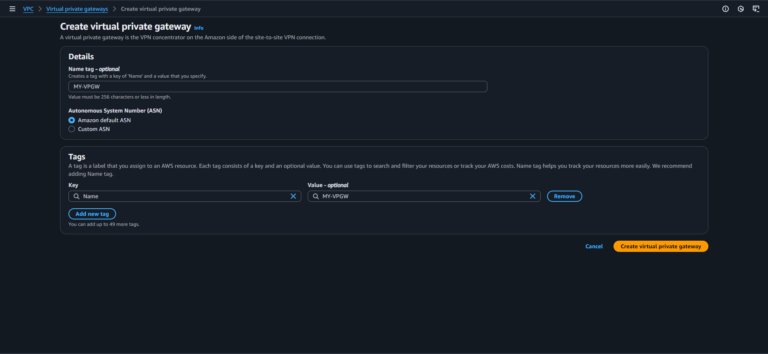
Navigate to the VPC Dashboard in the AWS and Select Virtual Private Gateways > Create Virtual Private Gateway.
Select the created VGW, click Actions, and choose Attach to VPC. Select your target VPC (e.g., 172.31.0.0/16).
Enable route propagation in the VPC route table to automatically propagate routes to the VGW.
Ensure your on-premise VPN device (e.g., Cisco, Juniper, or Fortinet router) has a static, internet-routable public IP address.
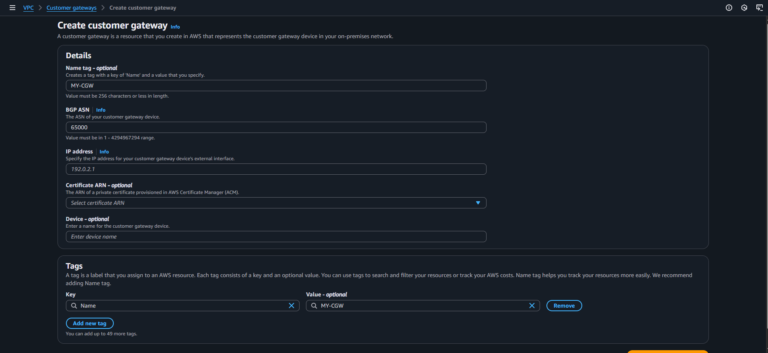
In the VPC Dashboard, go to Customer Gateways > Create Customer Gateway.
Enter a name (e.g., MyCGW), select Dynamic (BGP) or Static routing, and input the public IP of your on-premise VPN device.
If using BGP, provide the Autonomous System Number (ASN) for your on-premise device (default is 65000).
Go to VPN Connections > Create VPN Connection, Select the VGW and CGW created earlier.
Choose routing: Static (manually specify on-premise CIDR, e.g., 10.0.0.0/16) or Dynamic (BGP for automatic route exchange).
Configure tunnel options (e.g., IKEv2, AES-256 encryption, SHA-2 hashing) for security and Click Create VPN Connection.
- After creating the VPN connection, select it and click Download Configuration.
- Choose your on-premise VPN device vendor (e.g., Cisco, Juniper, Fortinet) and download the configuration file.
- Apply the configuration to your on-premise router/firewall. This typically includes IPsec settings, pre-shared keys, and tunnel endpoints.
In the VPC Dashboard, go to Route Tables and select the route table associated with your VPC’s private subnets.
Add a route for the on-premise network (e.g., 10.0.0.0/16) with the VGW as the target.
Ensure route propagation is enabled for dynamic routing.
- On your on-premise router, add a route for the AWS VPC CIDR (e.g., 172.31.0.0/16) to direct traffic through the VPN tunnel
- Verify the IPsec tunnel configuration matches AWS settings (e.g., encryption, authentication).
In the AWS Console, go to VPN Connections and check the tunnel status. Both tunnels (AWS creates two for redundancy) should show UP.
Use tools like ping or traceroute from an on-premise server to an EC2 instance’s private IP to confirm connectivity.
Setting Up AWS VPN Client
In the VPC Dashboard, go to Client VPN Endpoints > Create Client VPN Endpoint.
Choose a Client CIDR Range (e.g., 192.168.0.0/16) that doesn’t overlap with your VPC or on-premise networks.
Select Authentication Method: Use Active Directory (if integrated) or Certificate-based authentication.
For certificate-based authentication, generate server and client certificates using OpenVPN EasyRSA or AWS Certificate Manager (ACM) Private CA.
Select the Client VPN Endpoint and click Associate.
Choose the target VPC and private subnets where your EC2 instances reside.
Apply security groups to control access to EC2 instances.
- In the Client VPN Endpoint, go to Authorization Rules > Add Authorization Rule.
- Specify the destination network (e.g., 172.31.0.0/16) and allow access for All Users or specific groups if using Active Directory.
- Download the Client VPN configuration file from the AWS Console.
- Install the AWS VPN Client on your device (available for Windows, macOS, and Linux).
- Import the configuration file into the AWS VPN Client.
- If using certificate-based authentication, import the client certificate and key into the AWS VPN Client.
- Open the AWS VPN Client, select the imported profile, and click Connect.
- Verify connectivity by pinging an EC2 instance’s private IP or accessing a service (e.g., SSH to 172.31.1.100).
Security Considerations
Site-to-Site VPN:
Use strong encryption (AES-256, SHA-2, Diffie-Hellman group 14 or higher).
Enable Dead Peer Detection (DPD) to monitor tunnel health.
Restrict security groups and Network ACLs (NACLs) to allow traffic only from the on-premise CIDR (e.g., 10.0.0.0/16).
Use AWS CloudWatch to monitor tunnel status and set alarms for downtime.
Enable VPC Flow Logs to track traffic for auditing and troubleshooting.
AWS VPN Client:
Use certificate-based authentication for stronger security over username/password.
Regularly rotate client certificates to minimize risks.
Restrict Client VPN Endpoint access to specific subnets and services.
Monitor connection logs in CloudWatch for unauthorized access attempts.
Benefits
Site-to-Site VPN:
Secure: IPsec encryption ensures data confidentiality and integrity.
Cost-effective: No need for dedicated hardware or leased lines like AWS Direct Connect.
Scalable: Connect multiple on-premise locations to AWS using a single VGW or Transit Gateway.
Quick Setup: Deployable in under an hour with proper planning.
AWS VPN Client:
User-Friendly: Simple setup for remote users with minimal configuration.
Flexible: Supports multiple operating systems and integrates with existing identity providers.
Secure: Encrypts traffic to prevent interception on public networks.
Limitations & Alternatives
Site-to-Site VPN
Limitation | Description |
|---|---|
Latency & Jitter | Dependent on internet quality, which may affect performance for latency-sensitive applications. |
Bandwidth | Limited to ~1.25 Gbps per tunnel; lower than AWS Direct Connect. |
Single Point of Failure | Single tunnel failure can disrupt connectivity unless dual tunnels are configured. |
Alternative: AWS Direct Connect is a cloud service that establishes a dedicated network connection between your on-premise data center (or colocation facility) and AWS. Unlike Site-to-Site VPNs that rely on the public internet, Direct Connect provides a private, fiber-based connection that enhances security, stability, and performance.
This option is ideal for enterprises that:
Require consistent high throughput (e.g., data replication, media transfer, large backups).
Need lower latency than what a VPN over the internet can offer.
Want to bypass internet congestion and reduce exposure to internet-based threats.
Handle high volumes of traffic across hybrid environments.
AWS VPN Client
Limitation | Description |
|---|---|
Scalability | Best for individual or small team access, not large-scale network connectivity. |
Performance | Internet-based, so performance depends on user’s network quality. |
Alternative: Use AWS WorkSpaces or Remote Desktop Gateway (RD Gateway) for consistent desktop access, especially if users need persistent sessions or graphical environments.
AWS WorkSpaces: AWS WorkSpaces is a managed Desktop-as-a-Service (DaaS) solution that provides users with Windows or Linux desktops hosted in the cloud. It’s particularly useful for remote employees, developers, or contractors who need full desktop environments with consistent performance.
Testing the Connection
Site-to-Site VPN:
Run ping <EC2_private_IP> from an on-premise server to verify connectivity.
Use ssh <EC2_private_IP> or telnet <EC2_private_IP> <port> to test application access.
Check tunnel status in the AWS Console (both tunnels should be UP).
Monitor CloudWatch logs for errors or dropped packets.
AWS VPN Client:
Connect using the AWS VPN Client and ping an EC2 instance’s private IP.
Test SSH (ssh <EC2_private_IP>) or RDP (mstsc /v:<EC2_private_IP>) to the EC2 instance.
Verify Client VPN Endpoint logs in CloudWatch for connection details.
Conclusion
AWS Site-to-Site VPN and AWS VPN Client provide robust solutions for secure, private connectivity between on-premise networks or individual devices and EC2 instances in a VPC. Site-to-Site VPN is ideal for large-scale hybrid cloud environments, while the AWS VPN Client suits remote workers or small teams. Both solutions offer strong encryption, cost-effectiveness, and quick deployment, enabling seamless integration with AWS resources.
For automation, consider using AWS CloudFormation or Terraform to streamline VPN setup. Need assistance with hybrid cloud architecture or VPN optimization? Contact us for expert guidance!
